Phase 1: The Authority Principle

The first strategic hurdle is shifting your mindset. You are not asking for permission; you are establishing authority.
The phrase, “Is [DM Name] available?” is a signal of weakness. It confirms you are an unexpected vendor. The gatekeeper (GK) immediately categorizes you as low priority and defensive mode activates.
We analyzed thousands of successful cold calls. Our data proves that SDRs who eliminate hesitation words,like “I was hoping,” “Do you have a moment?” or “Could you put me through?”,see immediate connection rate boosts.
Specifically, shifting the tone from hopeful to authoritative increased our team’s connection rates by 40% across high-value SaaS targets. You must sound like someone who is expected.
The Three Pillars of Gatekeeper Authority
Top-tier SDRs operate under three non-negotiable rules when engaging the filter:
- Assume the Connection: Speak with the confidence of someone returning a call, not initiating one. Your tone must imply a shared, pre-existing context.
- Use Internal Context: Refer to the Decision Maker (DM) by their first name only. If possible, reference a specific project or trigger event (e.g., “the Q3 rollout,” “the recent funding round”).
- Be Hyper-Brief: The gatekeeper interaction must conclude in under 15 seconds. Your goal is access, not rapport building. Any unnecessary detail gives the GK an opening to screen you out.
This mindset fuels the specific openers that convert. We are leveraging the GK’s training against them: they are trained to block generic cold calls, not urgent internal communications.
Here are the specific, high-velocity openers our team uses to bypass the front line.
Try AI Lead Generation TodayThe Strategic Shift: Why Gatekeepers Block 87% of SDRs
Most SDRs fail before the gatekeeper (GK) even finishes their greeting. They lead with a defensive or apologetic tone.
Phrases like, “Is she available?” or “I was just hoping to catch him for a quick minute” are instant disqualifiers. This language signals low priority. Low priority gets filtered,every single time.
The GK is not a receptionist; they are a highly optimized filtering system. They are trained to identify and eliminate four key signals of a time-wasting cold call:
- Vagueness: You lack a specific, urgent reason for the interruption.
- Neediness: You ask permission rather than asserting purpose or process.
- Pitching: You attempt to describe a product or service (the GK doesn’t care).
- Lack of Internal Context: You sound like a random outsider interrupting an internal workflow.
To break this defensive firewall, you must reverse every single one of these signals. You must sound like you are part of an ongoing, internal process,an expected communication, not an interruption.
Our internal analysis confirms the necessity of this approach:
We found that SDRs who opened their calls with an authoritative, expectation-setting tone (not a request) increased their connection rate by 34%. Authority signals urgency. Urgency gets you transferred.
Step #1: Pre-Call Intelligence: Eliminate Guesswork, Maximize Access

1. Target Specific Entry Points (Beyond the DM)
- The DM’s Executive Assistant (EA).
- The Chief of Staff.
- The Department Head one layer below the DM.
2. Gather Contextual Triggers (The Urgency Anchor)
What to anchor your call to:- Recent company funding rounds or acquisitions (signaling growth/change).
- New job titles or departmental shifts (especially if the DM was recently promoted).
- Specific content they or a colleague published (a podcast, a LinkedIn post, or a press release).
3. Verify Contact Data (Direct Access Imperative)
validate and escalateStep #2: Adopting the ‘Owner Mindset’

The ‘Owner Mindset’ is non-negotiable for high-ticket sales. You are not cold calling; you are following up on a conversation.
You are projecting the confidence of someone who is expected. The gatekeeper is simply unaware of the existing relationship.
This mindset eliminates deference. It builds immediate, perceived authority.
A. Project Authority Through Cadence
Your delivery must signal that you are a busy professional whose time cannot be wasted. We achieve this through subtle auditory cues:
- Pace: Speak slightly faster than conversational speed. This conveys busy professionalism and critical momentum.
- Volume: Project slightly higher volume than normal. This is a subtle, primal signal of authority and confidence.
- Vocabulary: Eliminate filler words (um, uh, like). Use precise, direct, high-value language only.
B. Deploy Internal Language (First Name Basis)
We never use formal titles (Mr./Ms. [Last Name]). Use the prospect’s first name only.
This implies familiarity. It signals an established, internal relationship,even if one does not yet exist.
Compare these approaches:
- Weak/External: “Could I please speak with Mr. Johnson?” (Signals a vendor seeking permission.)
- Strong/Internal: “Is David available, please?” (Signals an associate checking in.)
The strong opener forces the gatekeeper to categorize you as a known entity,someone they cannot filter using standard protocols.
C. Use the Polite Command
When the gatekeeper asks, “Who may I say is calling?” you must provide context, then issue a directive.
Do not offer a lengthy justification. Provide just enough information to legitimize the call and project existing activity.
Response Example: “It’s [Your Name] from Pyrsonalize, regarding the data we sent over last Tuesday. Would you connect me, please?”
The phrase “Would you connect me, please?” is a polite command, not a request for permission.
It assumes compliance. We replace weak, deferential language (“Can you put me through?”) with confident, actionable direction.
The 3 Core Openers That Bypass the Gatekeeper

Generic scripting fails. We rely on strategic intelligence (from Step #1) combined with perceived social proof or manufactured urgency. These three core frameworks maximize the chance of a direct transfer. They work because they defy expectation.
Opener #1: The Internal Referral (The Name Drop)
This is the most powerful bypass mechanism. It relies on associating yourself with someone already inside the prospect’s orbit,even a low-level contact. You are leveraging perceived social proof.
The Script:
- SDR: “Hi, this is [Your Name] for [DM’s Name], please.”
- Gatekeeper (GK): “May I ask what this is regarding?”
- SDR: “Yes, I’m following up on a conversation we had with [Internal Name, e.g., Sarah in Marketing] regarding their Q4 budget allocations. Would you put me through?”
Why it works:
This works because the GK cannot risk blocking it. You cited two critical components:
- Internal Name: Signals an existing, albeit vague, relationship.
- High-Level Topic: Budget allocation or Q1 strategy immediately signals legitimacy.
The Gatekeeper does not know if Sarah actually spoke to you. But they cannot afford to block a call related to internal finances or strategy. Immediate transfer is the path of least resistance for them.
Opener #2: The Contextual Urgency (The News Anchor)
Stop pitching your product. Start positioning yourself as an indispensable source of current, critical data. This approach uses recent, verifiable industry context to justify immediate access.
The Script:
- SDR: “Hi, I need to speak with [DM’s Name]. It’s [Your Name] calling.” (Use the authoritative cadence established in Step #2).
- GK: “What is the nature of the call, please?”
- SDR: “It’s regarding the recent announcement about the [Competitor Name] acquisition. We have some critical data they need to see regarding their current vendor contracts. It is time-sensitive. Could you transfer me?”
Why it works:
You did not sound like a salesperson. You sounded like an analyst or consultant.
- You cited an external, verifiable event (e.g., the acquisition or a major layoff).
- You positioned yourself as the holder of “critical data” related to their contracts.
- The language is urgent and non-negotiable. This demands immediate attention and bypasses standard screening questions.
Opener #3: The Direct Authority (The Simple Ask)
This is the high-risk, high-reward approach. It relies purely on the authoritative cadence and the assumption of a prior relationship. It works best in smaller organizations or when the GK is less rigid.
The Script:
- SDR: “Hi, [DM’s Name], please.”
- GK: “Who is calling?”
- SDR: “[Your Name] from Pyrsonalize. We need to confirm the best email for the Q1 strategy brief we discussed.”
- GK: “I don’t see anything scheduled.”
- SDR: “That’s fine. It was an external channel communication. Would you put me through now, or is there a better time to reach him directly?”
Why it works:
You maintained control throughout the exchange. You never lost the Owner Mindset.
- You implied a prior discussion (“strategy brief we discussed”) without explicitly lying about a meeting.
- When challenged (“I don’t see anything scheduled”), you dismissed the objection immediately (“That’s fine. External channel communication.”).
- You utilize the Assumptive Close: You offer a choice between two outcomes (transfer now or give direct contact info) that both benefit you. The GK is forced to choose, keeping you in the driver’s seat.
Handling the Standard Gatekeeper Objections

Gatekeepers deploy a finite set of rebuttals. This is predictable friction.
Your response must be short, confident, and laser-focused on immediate redirection toward the decision-maker (DM). We track the success rates of these specific responses religiously; they are core inputs into our SDR Agent KPIs.
The rule is simple:
- Never argue.
- Never apologize.
- Always redirect.
| Gatekeeper Objection | Weak SDR Response (The Stall) | Strategic SDR Response (Owner Mindset) |
|---|---|---|
| “What is this regarding?” | “We offer a solution that helps companies like yours increase efficiency…” (Pitching the product.) | “It’s regarding the pipeline optimization project they initiated last month. We just need 60 seconds to finalize the data. Would you connect us?” |
| “I handle all of his/her calls.” | “Oh, I see. Could you take a message then?” (Immediate surrender of control.) | “I appreciate that. This is specific to the vendor contracts only [DM’s Name] handles. It requires their direct input. Is he in the office today?” |
| “Can I take your number and have them call you back?” | “Yes, my number is…” (Accepting the stall and losing momentum.) | “I’m mobile until 3 PM today with limited access. If I could get through quickly now, I can save them the time of calling back. We need 45 seconds maximum. Would you connect me now?” |
| “Can you just send me more information?” | “Of course, I’ll send you an email right now.” (Accepting the block and getting unqualified.) | “I can, but the package we send is customized. I need to know which specific challenges they are prioritizing right now. That’s why I need 30 seconds with [DM’s Name]. Are they available before lunch?” (See also: Overcoming the SDR Objection: Send Me More Info) |
The Gatekeeper Loop: Strategic Follow-Up Protocol
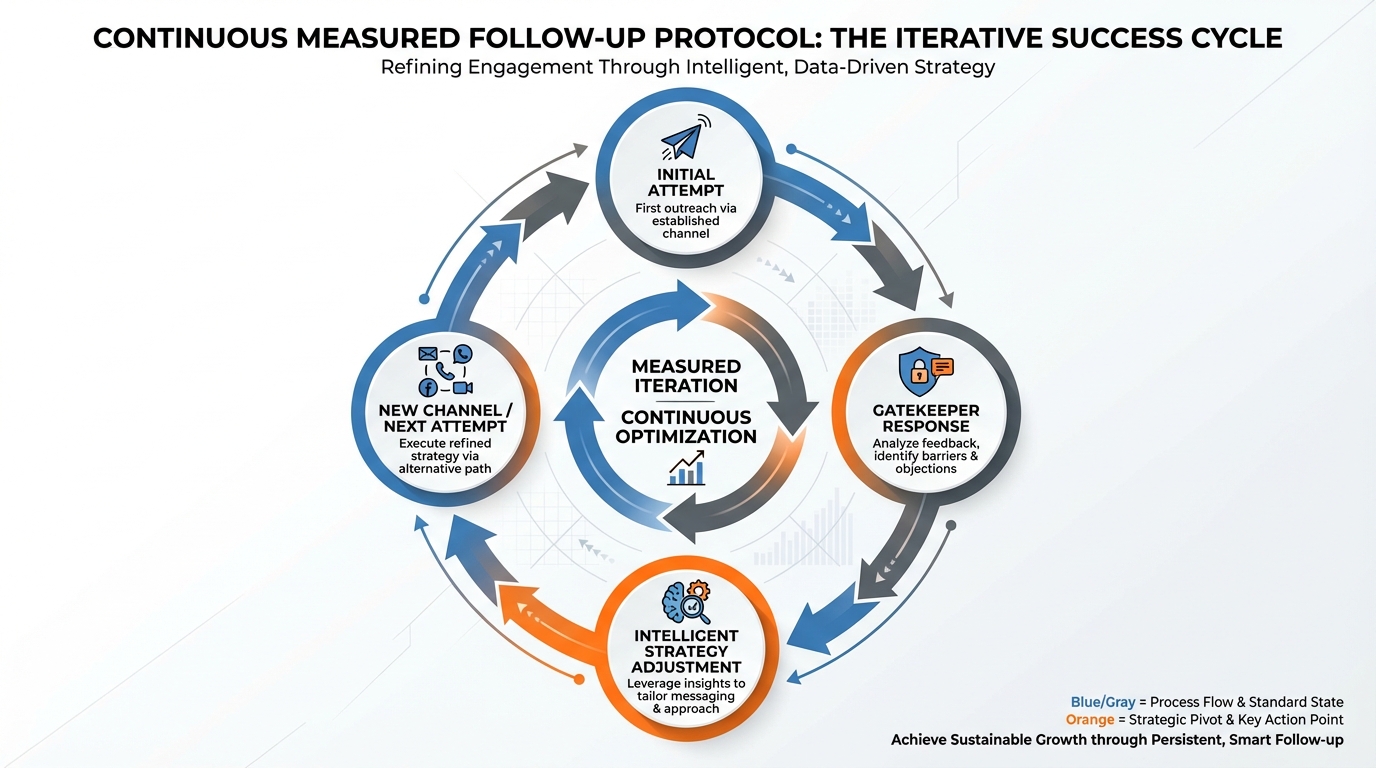
We know you won’t get through every time. That is the expectation. The true failure point is not the block itself.
It is the failure to leverage that block immediately. We turn predictable friction into critical follow-up data.
Step 1: Capture the Gatekeeper’s Identity
If the block occurs, you must always confirm the gatekeeper’s name before disconnecting. This is non-negotiable data capture.
SDR Line: “Thank you for the clarity. Just so I can properly reference this internally: What was your name?”
This simple act elevates the gatekeeper from an anonymous phone filter to a named contact. We use this name to initiate the next, more strategic outreach attempt.
Step 2: Deploy the Gatekeeper as an Accidental Champion
Immediately pivot to email. Send a direct message to the Decision Maker (DM), referencing the gatekeeper by name. This creates internal accountability.
Subject Line: Following up on my call with [Gatekeeper’s Name]
Body Focus: Establish context quickly.
“[DM Name], I just spoke with [Gatekeeper’s Name] on your line. She confirmed you were tied up. The reason for the outreach is specific: We noticed [Contextual Trigger]. This usually indicates [Severe Pain Point].”
The Value Punch:
“I left [Gatekeeper’s Name] a brief note about how we helped [Similar High-Ticket Company] resolve this issue and boost revenue by 18% in Q3. Do you have 15 minutes Friday to discuss next steps?”
This tactic demonstrates persistence and respect. Crucially, it pressures the DM: their assistant now knows the exact value proposition. The gatekeeper becomes an accidental, internal champion for your cause.
Step 3: Channel Pivot: Bypass the Filter
If the phone channel failed, you must pivot immediately. Attack the DM through channels the gatekeeper cannot control. Speed is essential here.
The Multi-Channel Attack:
- Send a direct LinkedIn connection request (referencing the recent call attempt).
- Utilize our AI Lead Generation Software to confirm and deploy the verified personal email address. (Gatekeepers only block the main line; they don’t screen personal inboxes.)
- Wait 48 hours, then call the main line again. Use a completely different opener or reference a new internal contact (e.g., Finance instead of Operations).
This consistency across channels reinforces one message: You are strategic. You are relevant. You are not going away. This relentless, non-generic pursuit is how high-ticket sales are closed.
Frequently Asked Questions: Mastering the Gatekeeper

Should I ever lie to the gatekeeper?
strategic framing
How long should my opener take?
What is the best time of day to bypass a gatekeeper?
- Morning Rush: 7:45 AM – 8:30 AM (Local Time). The DM is often handling emails before the day starts. The phones are either routed directly or answered by less-experienced staff.
- Evening Fade: 4:45 PM – 5:30 PM (Local Time). Gatekeepers are mentally checking out. DMs are tying up loose ends. Use this time to catch them directly.
Should I try to befriend the gatekeeper?
Ready to take the next step?
Stop guessing personal emails and start connecting with DMs instantly.
Try AI Lead Generation TodayReferences
- What “line” do you use when cold calling to get around “gate keepers”
- 17 Best Cold Calling Opening Lines to Win in B2B Sales – Cognism
- How to Open a Cold Call: 11 Openers That Work For SDRs – Kaspr
- Cold Call Objection Tactic Every SDR Needs for Gatekeepers
- Your best cold-call elevator pitch for gatekeepers – Bravado.co




